At the same time the world has struggled to overcome a devastating pandemic, cyber criminals and state-sponsored hackers have taken advantage of the growing convergence of corporate IT and the operational technology (OT) that runs factory and facility systems.
Increasingly, ransomware attacks, such as the one that struck North America’s biggest oil pipeline in early May, grab the major headlines. Yet, at the same time, cyber attacks on less visible and seemingly less accessible OT systems are growing in frequency and scope.
To help counter this trend, FM Approvals has joined the ISASecure certification assessment scheme developed and administered by the ISA Security Compliance Institute (ISCI), a non-profit subsidiary of the International Society of Automation (ISA). In order to provide third-party cybersecurity certification for industrial automation and control system (IACS) components and associated security development lifecycles, FM Approvals is undergoing the accreditation process to become an ISASecure Certification Body. In addition, FM Approvals is working with the Standards Council of Canada (SCC) to add the required ISA/IEC 62443 standards to its testing and certification scopes.
The new cybersecurity certification program is based at the FM Approvals headquarters in Norwood, Massachusetts, USA. A new cybersecurity laboratory (fig 1) and associated conference facility has been built there to support the new program.

Global standard
IACS components, such as embedded devices, network components, host components and software applications, will be evaluated and, for those that qualify, FM Approved based on the ISA/IEC 62443 series of standards developed by the ISA99 committee as American National Standards and adopted globally by the International Electrotechnical Commission (IEC).
“Cybersecurity is so new and essentially unregulated at this point,” notes Patrick Byrne, FM Approvals assistant vice president and technical team manager. “Industry and insurers are starting to understand that cyber crime is not limited to personal data theft and information loss. It now extends to the shop floor, to facilities management, to process control and beyond.”
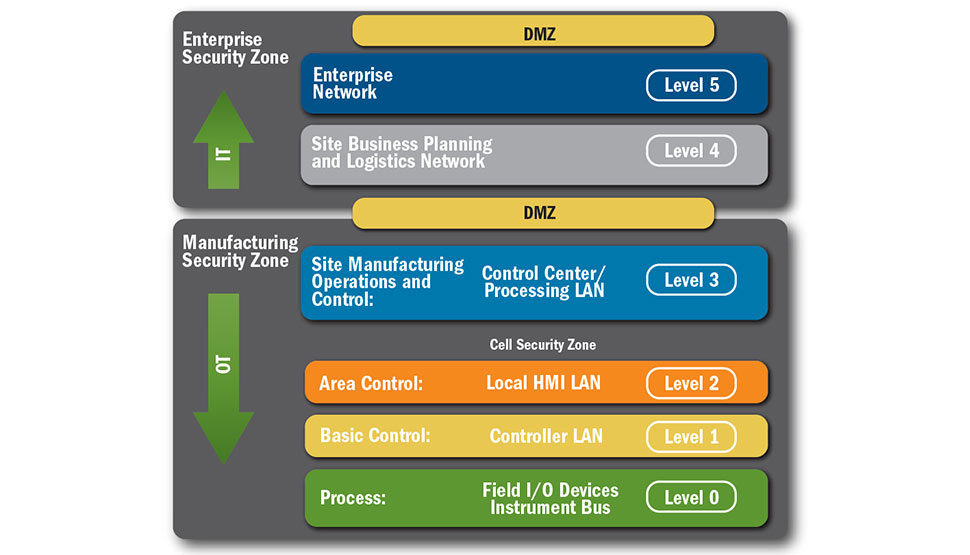
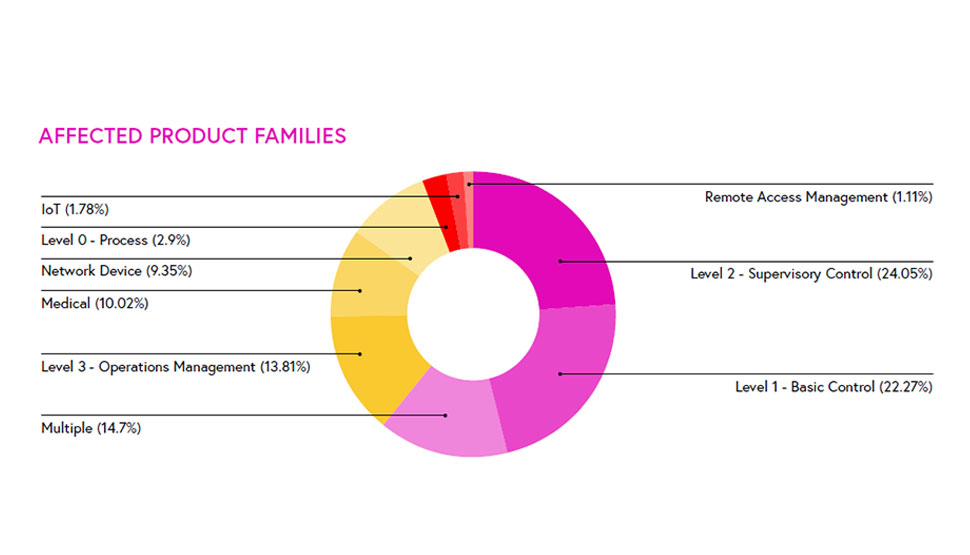
In fact, according to global cybersecurity experts Claroty, during the second half of 2020 more than 70 percent of industrial control system (ICS) vulnerabilities disclosed were remotely exploitable. More than 46 percent of vulnerabilities found affect the Basic Control (Level 1) and Supervisory Control (Level 2) levels of the Purdue Model (fig 2). Critical manufacturing, energy, water and wastewater, and commercial facilities—all designated as critical infrastructure sectors—were by far the most impacted by the vulnerabilities disclosed (fig 3).
Cyber crime on rise
In February, cyber criminals hacked into the controls of a water supply system for a small Florida town near Tampa Bay and attempted to raise the levels of sodium hydroxide or “lye” by more than 100 fold. Luckily, the attack was discovered before it could reach the water supply.
Many cyber attacks on OT systems have occurred around the world, including the 2017 attack on safety instrumented systems at a Saudi Arabia petrochemical plant that was caught just in time. In 2016, malware known as Crashoverride or Industroyer was used to attack and briefly disable part of the power grid supplying the Ukrainian city of Kiev.
One of earliest and most public examples of OT cyber attacks was the 2010 Stuxnet computer worm that targeted the supervisory control and data acquisition (SCADA) systems used to control the Iranian nuclear program. The worm targeted specific programmable logic controllers (PLCs) and physically damaged approximately 1,000 centrifuges used to refine nuclear material. It has been noted that variations of Stuxnet malware could be used to attack other SCADA systems around the world.
“Our program will provide third-party assurance that the applicable requirements of ISA/IEC 62443 have been met,” explains FM Approvals senior engineer Khalid Ansari, who is heading up the new cyber security lab in Norwood. The new cyber lab (Fig1 ) is isolated from the FM Approvals corporate network to ensure its cyber safety.
The availability of FM Approved ICS components signals to end users that the component meets certain standards with respect to known vulnerabilities and weaknesses, provides an easy way of specifying security needs by including certified products in RFPs, and reduces time spent on testing security during factory or site acceptance testing (FAT/SAT).
IACS systems and components will be evaluated based on three key parts of the ISA/IEC 62443 family of standards:
62443 part 4-1 -- Security Development Lifecycle Assurance (SDLA) – a certification that the Product Supplier’s security development lifecycle meets the requirements of ISA/IEC-62443-4-1.
62443 part 4-2 – Component Security Assurance (CSA) – a certification that the IACS Component meets the technical security requirements for IACS components included in ISA/IEC-62443-4-2 and has been developed using SDLA certified processes. IACS Components include embedded devices, host devices, network devices and software applications.
62443 part 3-3 -- System Security Assurance (SSA) – a certification that the IACS System meets the requirements of ISA/IEC-62443-3-3 system security requirements and security levels, and has been developed using SDLA certified processes.
New lab ready
Ansari notes that his group has developed a software tool that enables the accurate and rapid selection of appropriate test requirements from among the more than 170 possible tests included in the ISA/IEC 62443 scheme. The tool saves time in preparing proposals and executing cost-effective certification programs.
“It’s interesting and instructive to note that during the commissioning of our new cyber security lab, we discovered a vulnerability in one of the off-the-shelf PLCs we were using for our initial tests,” Ansari says. “Even though this was an older vulnerability, and the manufacturer was already aware of it that particular model of PLC is still likely available from the wide network of distributors that carry it.”
It should be noted that shop floor devices such as PLCs can have very long lifespans—10 years or more. Ansari adds, “If this PLC had undergone certification testing, this weakness would have been caught. This exemplifies the importance of independent testing and end-users demanding certified products. With the certified SDLA (Security Development Lifecycle Assurance) processes in place, the PLC manufacturer would be bound to inform the users and issue timely patches for such vulnerabilities.”
FM Approvals’ Patrick Byrne notes, “Cybersecurity is a new exposure for many organizations and can lead to serious consequences including business shutdowns, physical loses, damaged reputations, and personal harm. We can provide the third-party assurance that OT systems are safe from known threats. For manufacturers with multiple certifications, we can also offer a savings in time and costs by combining those certifications and thereby save time on reoccurring audits and administrative overhead.”
The new FM Approvals cybersecurity laboratory is ready to accept a wide range of IACS products and systems from manufacturers and suppliers worldwide. To learn more about this new FM Approvals certification program, please contact Khalid Ansari or visit FM Approvals.

